In recent weeks, I’ve encountered a sophisticated and targeted type of cyberattack that has severely disrupted the functionality of my website. As someone who has managed servers and websites for over 25 years, I’ve faced my fair share of Distributed Denial of Service (DoS) attacks. However, this new attack method is different and particularly concerning, especially for politically motivated or outspoken websites. In our case, the attacks started when the Long Live Trump Sale was launched.
Promise Us You Will Restore NTP Funding & Update FCC Safety Guidelines
- 08/01 – Make Politics About Health, Not Hatred: Democrat Policies Harm Children!
- What Are We Doing To Our Children? Why? Why Don’t You Care?
The Nature of the Stealth FDOS Attack I Have Encountered
This attack specifically targets WooCommerce session data, leading to what I’m calling a Financial Denial of Service (FDOS) attack. Unlike typical DoS attacks that render a server inaccessible, this FDOS attack focuses on overwhelming the WooCommerce sessions table. Here’s how it works:
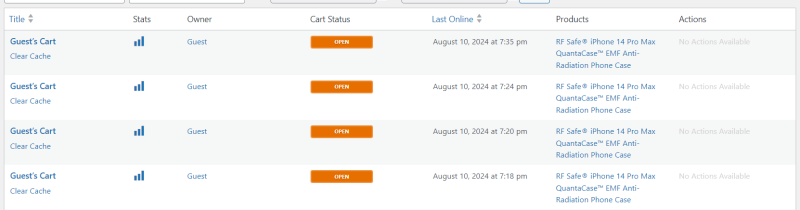
- Targeted Product Attack: Instead of a generic attack on the entire site, the attackers have zeroed in on a specific product. This focused attack leads to an enormous buildup of session data.
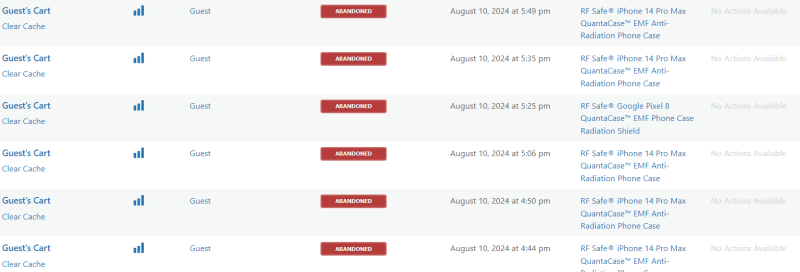
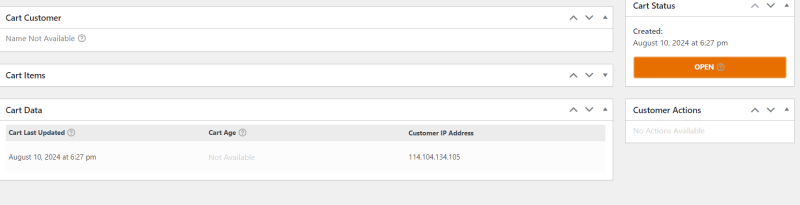
- Session Data Overload: The excessive session data fills up the WooCommerce sessions table, causing significant slowdowns and preventing users from completing checkouts. In my case, I had to clear out 60 to 100 MB of session data regularly.
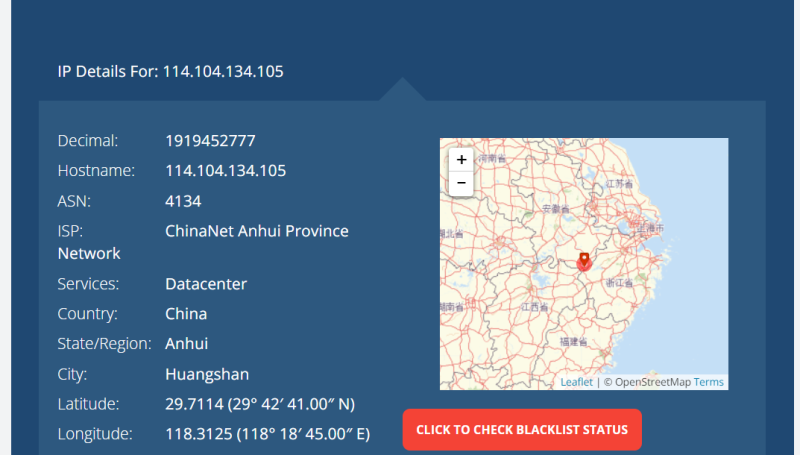
- Stealthy IP Masking: Despite blocking all of China at the server level, the attackers are still able to use Chinese IP addresses, indicating the use of sophisticated methods to bypass IP blocking.
- Resource-Intensive Attack: The attack uses IP addresses from very different blocks, suggesting significant resources and organization behind it, far beyond the capabilities of average attackers.
- Persistent Sessions: Each product is added to the cart by a different IP address, and the session is kept alive as if it were a legitimate user interaction, making it difficult to detect through typical rate limiting or IP blocking.
Uncovering the Attack
This attack is highly stealthy and can easily go unnoticed. Here are steps to uncover if your website is under an FDOS attack:
- Monitor WooCommerce Sessions Table: Look for a bloated WooCommerce sessions table. This is a clear indicator that an excessive number of sessions are being created.
- Track Cart Additions: Install a shopping cart plugin or build your own monitoring tool to track which products are being added to carts. In my experience, the attack targeted a single product, which was added to the cart hundreds of times via different IP addresses from various IP blocks.
Potential Political Motivation
Interestingly, the FDOS attack on my website began shortly after I publicly expressed support for Donald Trump. While it’s difficult to definitively attribute the attack to a specific entity, the pattern suggests a level of organization and resources that go beyond typical cyberattacks. Politically motivated websites, particularly those that are outspoken or controversial, might be at increased risk of similar attacks.
Why This Matters
FDOS attacks represent a significant threat to e-commerce websites, particularly those with political motivations or controversial content. If your website has experienced a sudden and extreme drop in sales or site performance, it’s crucial to investigate the possibility of an FDOS attack. These attacks can be easily overlooked, as they don’t follow the more obvious patterns of traditional DDoS attacks.
Mitigation Strategies
To protect your website from such attacks, consider implementing the following measures:
- Enhanced IP Blocking and Real-Time Threat Intelligence: Use services that provide advanced IP reputation filtering and real-time threat intelligence.
- Session Management: Regularly clean up old session data and shorten session expiration times.
- Monitoring and Alerts: Set up monitoring tools to alert you of unusual activity.
Call to Action
If you manage a politically motivated or outspoken website and have seen a sharp decline in sales or performance, I urge you to look into your WooCommerce session data. It might be the unseen culprit behind your issues. Let’s stay vigilant and protect our platforms from those who seek to silence us through underhanded tactics.
China Blocked At Sever Level Makes No Difference – all session data traces back to CN IPs

How to recover from FDoS attack by clearing the bloated sessions table – Mine has reached 100mb in a fairly short amount of time
wp-admin/admin.php?page=wc-status&tab=tools
The program used for the attack seems to have been given a product URL to attack.
Every one of the IPs comes from a China IP, even though China is blacklisted at a server level.
The Perfect Disrupter
FDOS attacks are particularly insidious because they blend in with regular traffic, making them difficult to detect. Unlike high-volume DDoS attacks that are noisy and obvious, FDOS attacks are stealthy, short in duration, and low in volume, aligning with the characteristics of the “Trojan horse” DDoS attacks described by Sean Newman.
Sean Newman’s Insights on Stealthy DDoS Attacks
Overview
Sean Newman’s 2019 article in Network Security, “Under the Radar: The Danger of Stealthy DDoS Attacks,” highlights the growing threat of short-duration, low-volume DDoS attacks. These attacks often go unnoticed because they are masked by the organization’s regular traffic flow. Newman’s insights provide a valuable framework for understanding the stealth FDOS attacks I have encountered.
Key Points from Newman’s Article
- Evasion of Detection: Stealthy DDoS attacks are designed to evade detection by most legacy and homegrown DDoS mitigation tools. They are swift, sometimes lasting just a few minutes, and almost always less than an hour.
- Underestimating the Threat: Organizations that focus solely on large-scale DDoS attacks are at greater risk of falling victim to these stealthier attacks. The short duration and low volume of these attacks make them hard to detect and mitigate.
- Increased Automation: The automation of attacks has made DDoS a cheap and accessible method for cybercriminals. This trend is likely to continue, increasing the frequency and sophistication of stealthy DDoS attacks.
- Cover-Up Tactics: Short, low-volume attacks are often used to cover up other malicious activities, such as malware planting or data exfiltration.
Application to FDOS Attacks
The FDOS attacks I have encountered share many characteristics with the stealthy DDoS attacks Newman describes. Both types of attacks are:
- Short in Duration: FDOS attacks typically occur over a short period, making them difficult to detect and respond to in real-time.
- Low in Volume: The attacks generate just enough traffic to overload the session management system without triggering typical DDoS defenses.
- Highly Stealthy: By blending in with normal traffic and using sophisticated IP masking techniques, these attacks evade traditional detection methods.
Uncovering the Attack
Detecting an FDOS attack requires a proactive approach and specialized tools. Here are some steps to uncover if your website is under an FDOS attack:
Monitoring WooCommerce Sessions Table
A bloated WooCommerce sessions table is a clear indicator of an FDOS attack. Regularly monitor this table for excessive session data. Unusual spikes in the size of this table should raise red flags.
Tracking Cart Additions
Install a shopping cart plugin or build a custom monitoring tool to track which products are being added to carts. If a single product is being added to the cart hundreds of times from different IP addresses, it is likely that your site is under attack.
Analyzing IP Addresses
Although the attackers may use sophisticated IP masking techniques, analyzing the IP addresses involved in the session creation can provide valuable insights. Look for patterns such as the use of IP addresses from different blocks and geographic locations, especially if you have blocked certain regions at the server level.
Mitigation Strategies
To protect your website from FDOS attacks, consider implementing the following measures:
Enhanced IP Blocking and Real-Time Threat Intelligence
Use services that provide advanced IP reputation filtering and real-time threat intelligence. These services can help detect and block malicious IP addresses more effectively than standard IP blocking methods.
Session Management
Regularly clean up old session data and shorten session expiration times. This reduces the risk of session data overload and helps maintain optimal website performance.
Monitoring and Alerts
Set up monitoring tools to alert you of unusual activity. Tools like New Relic, Datadog, or custom scripts can help detect abnormal patterns in session data and cart additions.
Anomaly Detection
Implement systems that use machine learning to detect abnormal patterns in web traffic and user behavior. These systems can identify suspicious activities that traditional security measures might miss.
Advanced Bot Protection
Given the capabilities of modern AI to bypass traditional CAPTCHA, it’s essential to employ more advanced bot protection methods:
- Behavioral Analysis: Use tools that analyze user behavior to detect bots. Bots often behave differently from human users, and advanced behavioral analysis can identify these differences.
- Challenge-Response Tests: Implement more sophisticated challenge-response mechanisms that are harder for AI to bypass. This might include puzzles that require a deeper understanding of context or interactive elements that are difficult for bots to navigate.
- Device Fingerprinting: Use device fingerprinting techniques to track unique characteristics of devices accessing your site. This can help identify and block bots that attempt to disguise themselves as legitimate users.
- Rate Limiting Based on Behavior: Instead of traditional IP-based rate limiting, employ behavior-based rate limiting. For example, limit the number of times a specific action can be performed in a short period, such as adding an item to the cart, based on user behavior patterns.
- Bot Management Services: Consider using dedicated bot management services like Cloudflare Bot Management, PerimeterX, or Akamai Bot Manager. These services use advanced techniques to detect and mitigate bot traffic.
CAPTCHA and Bot Protection (Enhanced)
While traditional CAPTCHA methods may be bypassed by advanced AI, they can still be part of a multi-layered security approach. Combine CAPTCHA with other methods to create a more robust defense:
- Invisible CAPTCHA: Use invisible CAPTCHA solutions that run in the background, analyzing user interactions without disrupting the user experience. These solutions can flag suspicious behavior for further verification.
- Adaptive CAPTCHA: Implement CAPTCHA that adapts based on the user’s risk profile. For example, only show CAPTCHA to users exhibiting suspicious behavior or originating from high-risk regions.
Conclusion
The Stealth FDOS attack is a perfect disrupter hidden in session data. By blending in with regular traffic and using sophisticated IP masking techniques, these attacks can evade traditional detection methods and cause significant disruptions to e-commerce websites. Drawing on the insights from Sean Newman’s article on stealthy DDoS attacks, this report highlights the need for proactive monitoring and advanced security measures to protect against FDOS attacks.
If you manage a politically motivated or outspoken website and have seen a sharp decline in sales or performance, I urge you to investigate the possibility of an FDOS attack. Let’s stay vigilant and protect our platforms from those who seek to silence us through underhanded tactics.